At DEF CON, security researcher and SquareX founder Vivek Ramachandran unveiled a critical vulnerability in Secure Web Gateways (SWGs), shaking the confidence in a key part of enterprise security. Despite their name, every SWG in Gartner’s Magic Quadrant for SASE and SSE can be bypassed, allowing attackers to deliver malware undetected.
Ramachandran, who has identified over 25 different bypass methods, has termed his technique “last-mile reassembly.” The idea is simple but alarming: attackers exploit the browser’s computational capabilities to reassemble malicious code at the last moment, bypassing SWGs entirely. This method involves breaking malware into small, unrecognizable pieces and using modern web technologies like Web Assembly. The SWGs, outdated and not designed to handle today’s complex web browsers, often fail to raise any alarms.
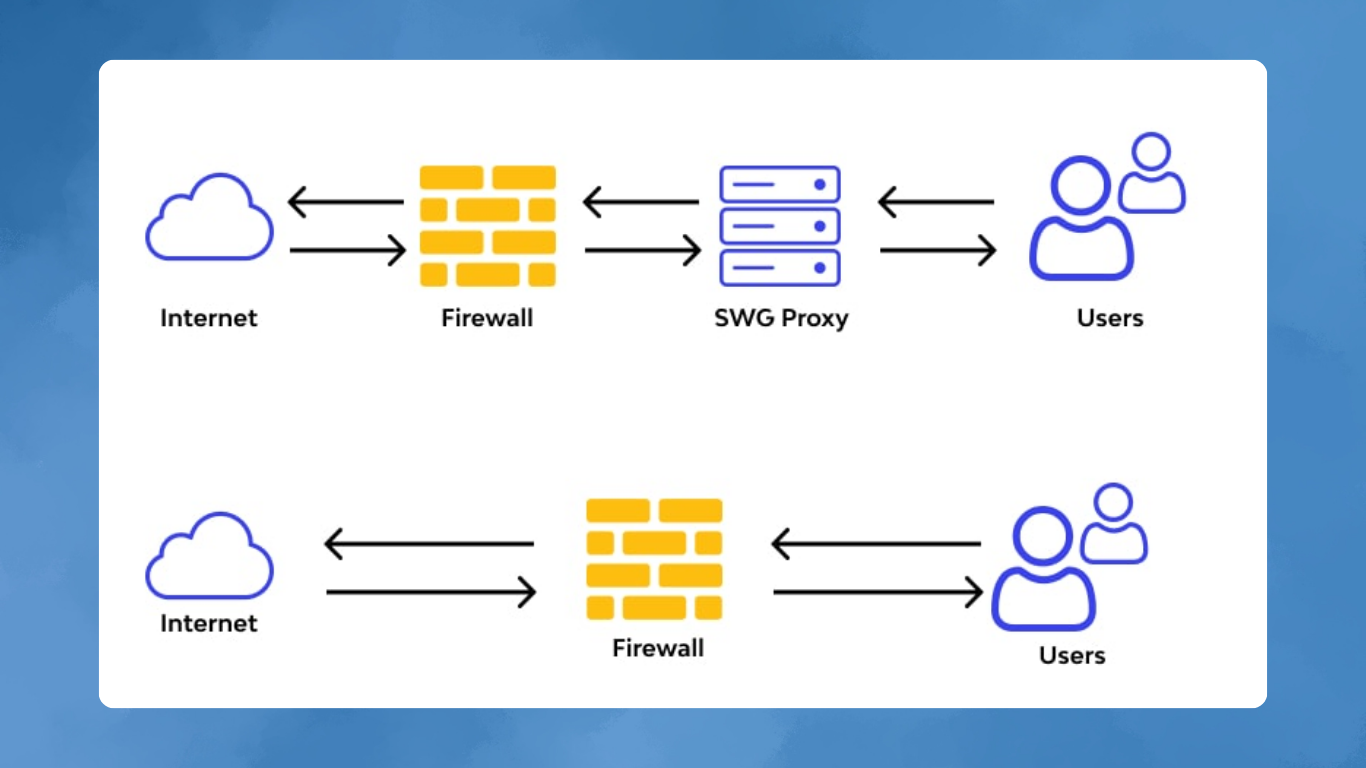
Originally, SWGs were built as SSL intercepting proxies about 15-17 years ago. Over time, they evolved into cloud-based security solutions. However, this evolution introduced significant vulnerabilities. SWGs primarily rely on detecting application-layer attacks from network traffic before it reaches the browser. If the traffic doesn’t appear overtly malicious, the SWG might let it through, inadvertently delivering malware to the user’s browser.
Ramachandran pointed out that these vulnerabilities are deeply rooted in the architecture of SWGs, making it almost impossible for vendors to fix them without a complete overhaul. He emphasized that relying solely on cloud-based solutions to address these issues is futile, as it undermines the entire cloud security model.
The problem is compounded by the fact that SWGs often leave numerous channels unmonitored, such as gRPC, WebRTC, WebSocket, and WebTorrent. Attackers can easily exploit these gaps to smuggle malware past the gateway.

Ramachandran didn’t name specific vendors but urged security professionals to reconsider their reliance on SWGs. He warned that many organizations might not have adequate endpoint security because SWG vendors often market their solutions as sufficient, claiming that cloud filtering alone is enough.
To help companies assess their vulnerabilities, SquareX is releasing a free tool to test SWGs against these advanced bypass methods. Ramachandran’s advice is clear: focus on endpoint security. Since the attacks happen in the browser, that’s where they need to be detected.
In summary, last-mile reassembly attacks highlight a significant flaw in current SWG technology. Enterprises must rethink their security strategies, as SWGs alone aren’t enough to protect against these sophisticated attacks.

Subtly charming pop culture geek. Amateur analyst. Freelance tv buff. Coffee lover